Single Sign-On (SSO) is an authentication process that allows a user to access multiple applications with one set of login credentials.
OneLogin’s Trusted Experience Platform provides everything you need to secure your workforce, customer, and partner data.
Purpose
The purpose of the article is to provide a guide on how to configure SSO with OneLogin.
Prerequisites
To configure settings on the OnLogin server, we need to add an assertion URL in which the account ID is encrypted.
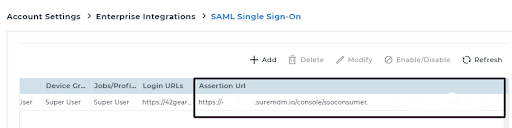
- Login to the SureMDM console > Settings > Account Settings > Enterprise Integrations > SAML (Single Sign On) > Configure OneLogin and fill in the details as shown below to get the Assertion URL.
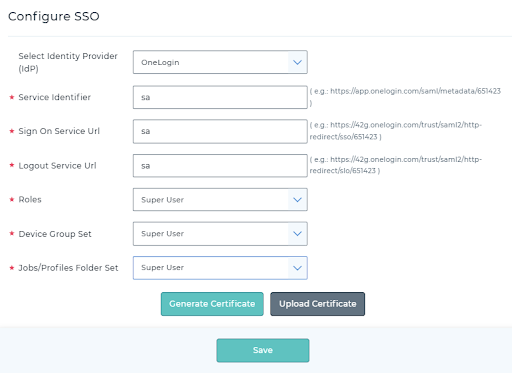
- Click Generate Certificate and save the configuration.
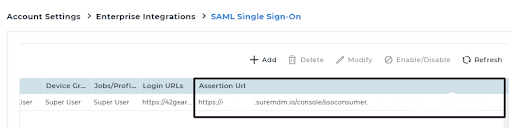
- After saving the configuration, we can copy the Assertion URL.
Steps
There are two steps involved in configuring SSO with the OneLogin server.
- Configure settings on the OneLogin server.
- Configure settings in the SureMDM Web Console.
Step 1 : To configure on One Login Server
1. Log in to one Login Server > Apps > Add Apps.
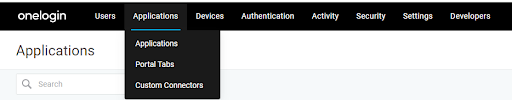
2. On the Search Tab, search for SAML applications.
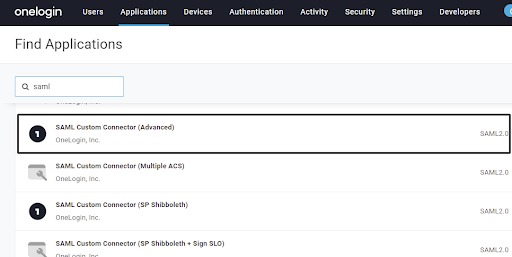
- Select SAML CustomConnector (Advanced).
- Create a new app with the name SureMDM and Save.
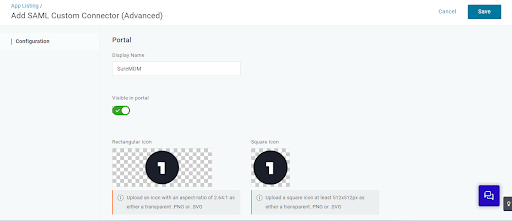
5. After saving, go to the Configuration section and add the values.
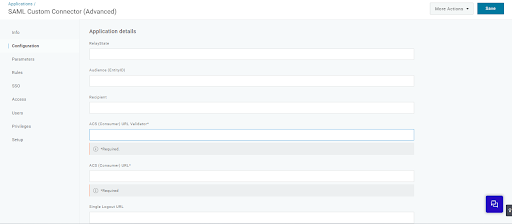
Audience (EntityID): urn:42gears:suremdm:SAML2ServiceProvider
Recipient: Assertion URL that we copied from the SureMDM console.
ACS (Consumer) URL Validator*: Assertion URL that we copied from the SureMDM console.
ACS (Consumer) URL*: Assertion URL that we copied from the SureMDM console.
For example,
https://suremdm.42gears.com/console/ssoconsumer/81b6b0f3-097b-4d4f-b2d8-fece8dc345cfhttps://(Serverpath)/console/ssoconsumer/(Encrypted account ID)NOTE: Encrypted Account ID can be found in the Assertion URL
Single Logout URL:
https://(SureMDM Serverpath)/console/ssoservice/(Encrypted account ID)For example,
https://suremdm.42gears.com/console/ssoservice/8lb6b0f3-097b-4d4f-b2d8-fece8dc345cf- Configure the above details and Save.
- Navigate to the SSO tab, change the SAML Signature Algorithm to SHA-256, and Save.
- Download SAML metadata from the More Actions section at the top of the page.
Step 2: To configure on SureMDM Server
- Log in to the SureMDM console using your Username and Password.
- Login to the SureMDM console > Settings > Account settings > Enterprise integrations > SAML (Single Sign On) > Click on Add and enter the following details from your metadata file:
Service URL: This value is present under EntityDescriptor tag, entityID property of your metadata XML file
Example:
https://app.onelogin.com/saml/metadata/588f1411-2345-4f01-bcdd-a435fef11f5eService Identifier: This value is present under EntityDescriptor > IDPSSODescriptor >
SingleSignOnService (node with HTTP-Redirect binding) > Location
Example:
https://2gears.onelogin.com/trust/saml2/http-redirect/sso/588f1411-2345-4f01-bcdd-a435fef11f5eSingleLogoutService (node with HTTP-Redirect binding) > Location
Example:
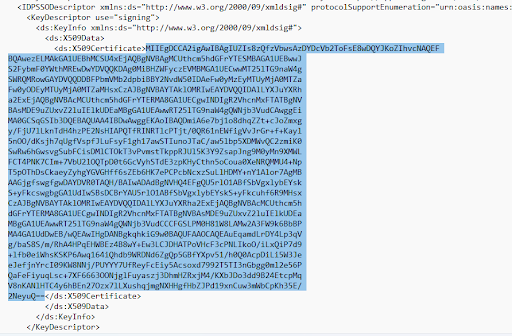
https://2gears.onelogin.com/trust/saml2/http-redirect/slo/2961456- Copy the text value present inside EntityDescriptor > KeyDescriptor > ds:KeyInfo > ds:X509Data > ds:X509 Certificate and save it in a file with extension.cer.
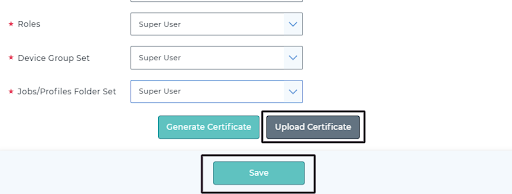
- Upload the .cer file by clicking on Upload Certificate. Keep the password field empty, and save the configurations.
- Users can login to the SureMDM console using OneLogin.
Need help? CONTACT US
