SureMDM now offers users to enroll devices using the PingFederate.
PingFederate is an enterprise federation server that enables user authentication and single sign-on. It serves as a global authentication authority that allows employees, customers, and partners to securely access all the applications they need from any device.
In order to enable PingFederate in SureMDM, follow the below-mentioned steps.
PingFederate User Configuration
Create a new SP adapter instance by logging in to the PingFederate administrative console.
- For PingFederate 10.1 or later: Go to Applications → Integration → SP Adapters. Click Create New Instance.
- For PingFederate 10.0 or earlier: Go to Service Provider → Adapters. Click Create New Instance.
Note: In the configurations, the values need not be explicitly specified. However, the default values can be accepted.
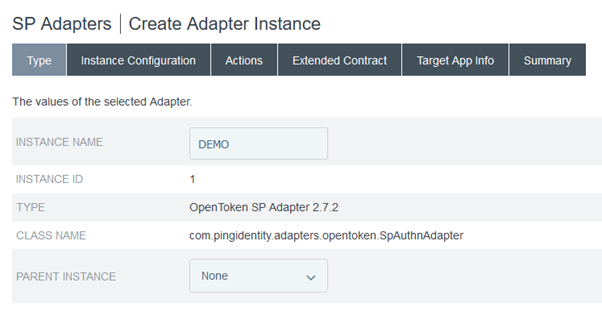
Transport Mode: Form POST
Cipher Suite: AES-128/CBC
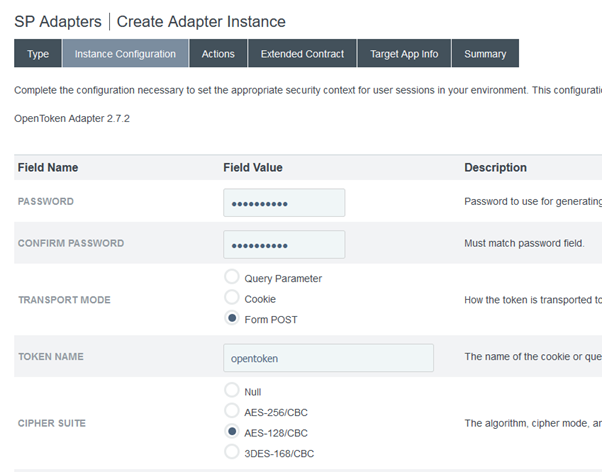
In the Core Contract mention it as “Subject” and under the Extended Contract specify Email Address, Name, and UserID as shown in the image below.
Create an IdP Connection which makes use of the SP Adapter created previously. This linking can be done from the Target Session Mapping -> Adapter Instance Name entry of the IdP Connection.
The Sign-On Service URL configuration in SureMDM will make use of this IdP Connection.
SureMDM console configuration
- Login to the SureMDMConsole
- Navigate to the Settings and further to Account Settings
- Select the Device Enrollment Rules
- Select Opentoken authentication for Device Authentication Type
- For Sign-On Service URL, provide the URL in the below format
https://pingfs.demo.42gears.com:9031/sp/startSSO.ping?PartnerIdpId=https://fs.demo.42gears.com/adfs/services/trust
• pingfs.demo.42gears.com:9031 should be replaced by the URL of the PingFederate server
• https://fs.demo.42gears.com/adfs/services/trust should be replaced by the ID of the IdP to which PingFederate delegates authentication.Note: SureMDM will automatically append the endpoint to which the SAML assertion should be posted in this URL. It will be appended using the “TargetResource” parameter.
- The Logout Service URL is not used as of now. But since it is a compulsory field, the admin can enter anything there, for example, XYZ
- For Agent Configuration, the admin can copy-paste the content of the SP Adapter agent configuration file from the PingFederate server.
For Example :
use-verbose-error-messages=false http-only=true cookie-path=/ token-renewuntil=43200 token-notbefore-tolerance=0 password=T5pgQt39sSp5g3yclV1eIw== token-name=opentoken use-cookie=false cipher-suite=2 use-sunjce=false token-lifetime=300 obfuscate-password=true track-authntime=true
For more details on our products, click here
