Digital certificates authenticate enterprise users and ensure secure access of corporate emails, Wi-Fi and other resources. SCEP (Simple Certificate Enrollment Protocol) is a convenient way to obtain digital certificates on a large scale and streamline endpoint authentication process. For this reason, most MDM systems integrate deeply with Certificate Authorities over SCEP, to automate endpoint authorization and authentication before granting them access to enterprise resources.
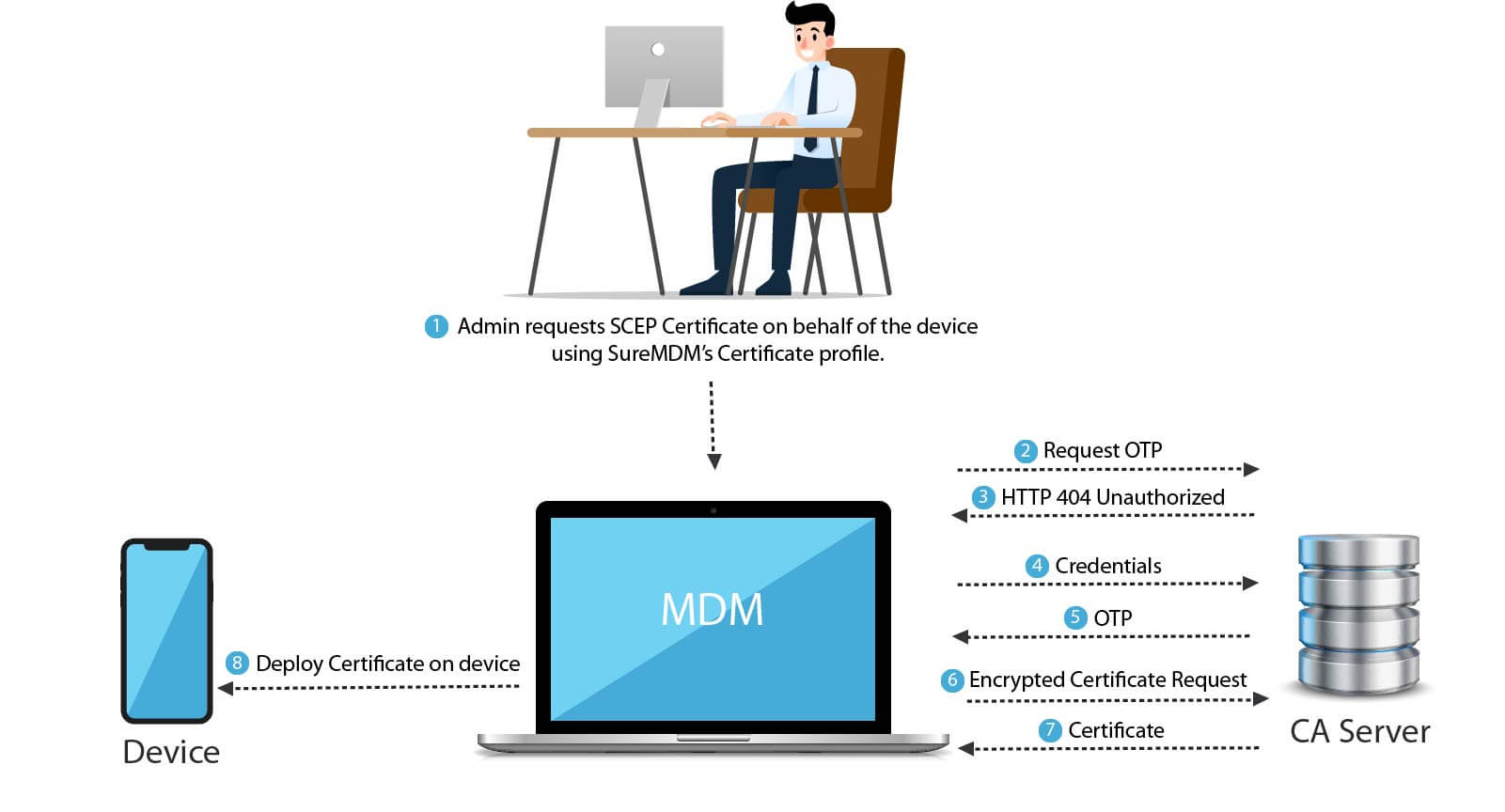
How EMM integrates with CA Server over SCEP?
To push a certificate on a device, an MDM administrator has to apply a profile containing a SCEP certificate to a device, the MDM server then contacts the CA server to obtain an OTP. The CA server responds with a HTTP 401 (Unauthorized) code. In response to this, the MDM server provides its credentials to the CA server. If the credentials are correct, the CA server then issues an OTP to the MDM server. The MDM server then creates an encrypted certificate request and sends it to the CA server along with the OTP. The CA server then issues a certificate to the MDM, which in turn applies it to the device.
Steps to integrate and push CA certificates from SureMDM
1. Configure Certificate Management in Account Settings
To get SCEP enrolled into the devices, the admin needs to login to SureMDM Web Console and go to Account Settings and click Certificate Management.
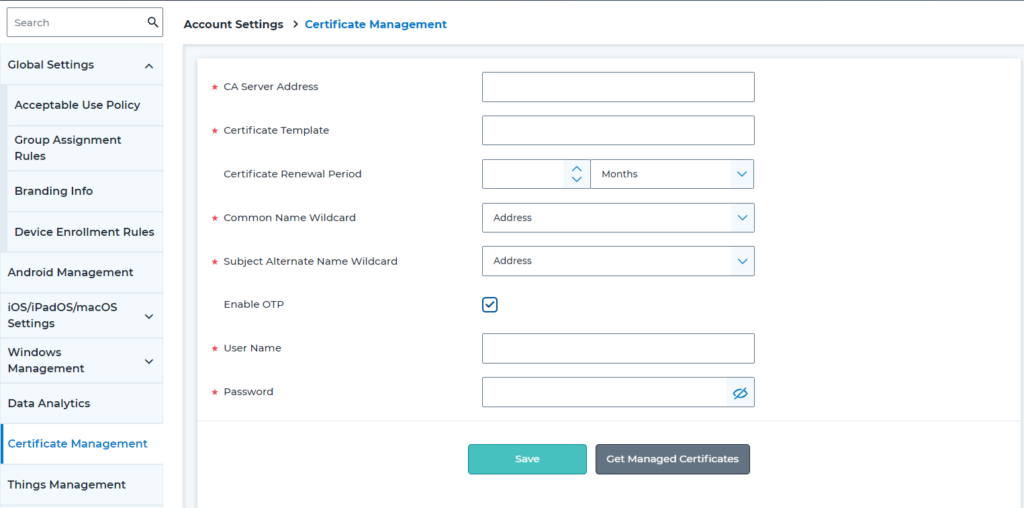
- A screen similar to the one below will appear which has the CA Server Address, Certificate Template, Certificate Renewal Period, Common Name Wildcard, and Subject Alternate Name Wildcard.
- Once all these fields are filled by the admin, check Enable OTP
- Enter the certificate Username and Password
- Click Save
Terms explained:
CA Server Address: Enter the complete address of the CA server here. This should also include “HTTP” or “HTTPS”, depending on the protocol used by the SCEP server (for example, https://servername.domain.com/certsrv/mscep/mscep.dll)
Certificate Template: This should contain the name (template name, not the display name) of a SCEP template that is configured on the CA server.
Certificate Renewal Period: Certificates that are about to expire within this time period in the future will be auto-renewed and pushed to devices.
Common Name (CN) wildcard and Subject Alternate Name (SAN) wildcard: This defines what the entries for CN and SAN should be in the certificates deployed using SCEP. These values are unique for each device and serve to identify a device during authentication. Possible values are:
- IMEI
- MAC Address
- DeviceID
- Serial number
- Constant Text: Can either be a constant hard-coded text, which will make it common for all devices, or a wildcard, which makes it unique per device. Supported wildcards are %emailaddress% (Email Address of the device user) and $devicename$ (device name as seen on the SureMDM device grid)
The “Enable OTP” field can be used to enable the SCEP challenge password feature. When using this feature, a user must first log in with their username and password to get a One-Time Password (OTP). The OTP will then be used in the certificate request to the SCEP server.
If the Enable OTP option is selected, the username and password fields must also be filled with the required information. SureMDM will use this to request for OTPs and use them.
2. Create a Profile and include certificate using SCEP
iOS/Android EMM profiles can be configured to include a SCEP certificate. For example, in iOS, go to Profiles, select iOS/iPadOS and select Certificate tab. A prompt will appear and check the Create Certificate Using SCEP option.
3. Use certificate for authenticating against enterprise resource
Once the certificate using SCEP is included in your profile, you can now use this certificate for authentication against enterprise resources like Wi-Fi, Email, etc.
For example, in the same profile mentioned in step no. 2 above, go to the Wi-Fi Configuration tab and configure it and then click Add. A window will prompt to enter the SSID, select Security Type supported as EAP/TLS, check the Certificate Based Authentication and Auto Join options and save it.
4. Push profile to devices
We can now save the above profile and apply it to any devices enrolled in SureMDM. Once pushed to the device, the SureMDM will query the CA server over SCEP to obtain a certificate for that device, bundle it in its payload and push it to the device. The MDM agent on the device will receive the payload, extract the certificate from it and install on the device, making it available for other apps like email client, VPN client, for authentication.
5. Verify certificate on device
Once the profile is successfully deployed, you can see the EMM installed certificates by going to the device Settings > General > Device Management.
Once the device is secured with SCEP certificate, in the case of any certificate being lost or leaked, the admin can revoke the particular certificate for that device without disturbing the other certificates and devices. This is the major advantage of having certificates per employee over the single gold certificate that works for all devices in the organization.
6. Renew and Revoke certificates
To renew or revoke any certificate, we need to go to Account Settings > Certificate Management > Get Managed Certificates. Here you can see a list of all the certificates issued by CA server on EMM request. The admin can choose to either Revoke or Renew these certificates from here. SureMDM can also auto renew the certificates on expiration.
In enterprises, employees are often allowed to bring their own devices at work. They access enterprise resources on their devices from anywhere which might put the corporate resources at risk. In addition to regular password based authentication, enterprises should bring in that extra layer of security through certification based authentication. This gives greater control and flexibility in the hands of IT admins.
With Certification Based Authentication (CBA), pushing certificates manually on multiple devices is time consuming and laborious. So integrating and automating this workflow using a MDM solution saves a lot of effort and time for IT admins. Organizations must ensure that the MDM solution they are using, properly integrates with certification authority servers.
SureMDM supports integration with most CA servers over SCEP, allowing seamless deployment of certificates to enterprise devices.
If you are looking for an MDM solution that can be integrated well with CA certificates, Try 42Gears’ SureMDM here.
